In this blog post, we will show you the ten most used SSH commands in any Linux distribution.
SSH stands for Secure Socket Shell and is one of the main key services in Linux. The default port that SSH is running on is the TCP/IP port 22, but it can be easily changed due to security reasons. System Administrators are using this system to log in to the server and execute commands via the command line. The SSH as the secure shell is a replacement for insecure login programs such as Telnet, rlogin, rsh and etc.
In this blog post, we will use the Ubuntu 22.04 OS. You can use any Linux distribution. Let’s get started!
Prerequisites
- Fresh install of Ubuntu 22.04 OS
- User privileges: root or non-root user with sudo privileges
Update the System
First, update the system packages to the latest versions available.
sudo apt update -y && sudo apt upgrade -y
Once the system is updated, we can start with the most 10 used SSH commands in Linux.
1. Log in to Server with root User
To login to the server with the root user, execute the following command:
ssh [email protected]
In this case you will log in to the server on the default port 22, where the access is granted. In most cases, this command is used on the hosts with multiple virtual private servers in other words, with virtualization.
2. Log in to Server with root User, password, and custom port
This scenario is used by the clients who have full root access to their servers provided by the hosting company.
ssh [email protected] -p 6622
This is a scenario where the SSH port is changed due to security reasons, and the SSH will be accessible only on that port.
3. Log in to Server with a non-root User
Clients who do not have full root access to the server can only log in with their username. In most cases, those users have shared hosting plans or are developers who have limited access to the server.
shh [email protected] -p 22
It is up to the user if he wants to specify or not the default port 22 in the command.
4. Log in to Server with Key File
In this case, the user has the key file somewhere locally on his computer. Executing the ssh command is with specifying the location of the key file and specifying the user that file has permission for.
ssh -i keyfile.txt [email protected]
The key file can be located on your server, and you can log in to another server as well.
5. Check SSH client version
We assume that we covered the most used cases for login to the server, so now will proceed with the SSH commands that are executed on the server.
To check the SSH client version, execute the following command:
ssh -V
You should receive an output similar to this
root@host:~# ssh -V OpenSSH_8.9p1 Ubuntu-3, OpenSSL 3.0.2 15 Mar 2022
6. Generate SSH Key Pairs
To generate SSH key pairs, follow the steps below. First, create the directory for the SSH keys.
mkdir /root/.ssh
Then, set the right permissions.
chmod 0700 /root/.ssh
Now, you can generate SSH keys with extra security using the command below:
ssh-keygen
The system will ask you where to store the keys, about the passphrase, and confirm the passphrase. Once done, you should receive an output similar to this.
root@host:~# ssh-keygen Generating public/private rsa key pair. Enter file in which to save the key (/root/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /root/.ssh/id_rsa Your public key has been saved in /root/.ssh/id_rsa.pub The key fingerprint is: SHA256:j/jQn0W8CrxJdR5NHcfTn9zDTmlANj4dn9QRlljNzWE [email protected] The key's randomart image is: +---[RSA 3072]----+ | .+oE@| | oo*+#| | o=oO| | . o.Oo| | S . = = .| | + + + o . | | o * . + | | + = + | | + + | +----[SHA256]-----+
7. Copy Files Remotely over SSH with Rsync
This command is often used when there is some website migration over two different servers.
For example, to copy the html directory from one to another server running on port 7022, execute the command below:
rsync -Waq -e 'ssh -p 7022' /var/www/html/ root@"IP address of the other server":/var/www/html/
8. Copy File Remotely over SSH with SCP
scp -p 7022 /path_of_the_file/name.txt username@"IP address of the other server":/var/www/html/
This command will copy the file to the /var/www/html directory on a server running on port 7022
9. Change Default SSH Port 22
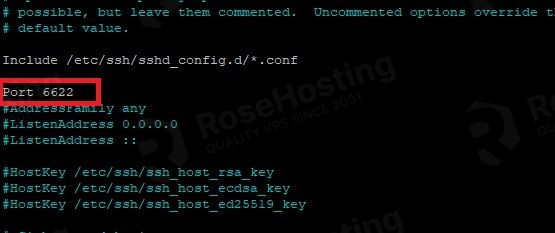
This is not an SSH command but is very relatable to the SSH service itself. Open the file /etc/ssh/sshd_config with your favorite editor and find the line that contains the Port 22
Change the port number to 6622 for example. Save the file and close it.
10. Restart SSH Service
After some changes in the SSH configuration, we need to restart the SSH service for the changes to take effectivity.
sudo systemctl restart ssh.service
That’s all. In this tutorial, we explained the ten most used SSH commands in Linux. If you find it difficult to understand the basic SSH commands, you can always contact our technical support, and they will help you with this. We are available 24/7.
If you liked this post about ten useful SSH commands in Linux, please share it with your friends on the social networks using the buttons on the left or simply leave a reply below.
